The latest and valid Cisco 200-201 exam practice questions are shared online
The Cisco 200-201 certification exam is to verify the candidate’s understanding of the Cisco Cybersecurity Operations Fundamentals (CBROPS), and the corresponding certification certificate can be obtained by reaching the passing score of the Cisco Certified CyberOps Associate certification.
Passing the Cisco 200-201 certification exam is not easy and the surest way is for candidates to practice to help them pass the exam.
I will share 15 latest and valid Cisco 200-201 exam practice questions to help candidates practice the test.
Candidates are welcome to select 200-201 dumps for 2023: https://www.leads4pass.com/200-201.html (contains the latest 264 exam questions and answers).
Cisco 200-201 Exam Practice Questions Read Online
| Type | Number of exam questions | Exam name | Exam code |
| Free | 15 | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) | 200-201 |
Question 1:
What describes a buffer overflow attack?
A. injecting new commands into existing buffers
B. fetching data from memory buffer registers
C. overloading a predefined amount of memory
D. suppressing the buffers in a process
Correct Answer: C
Question 2:
Which metric is used to capture the level of access needed to launch a successful attack?
A. privileges required
B. user interaction
C. attack complexity
D. attack vector
Correct Answer: D
Attack Vector ( AV) represents the level of access an attacker needs to have to exploit a vulnerability. It can assume four values: Network, Adjacent, Local, and Physical. Source: Official cert Guide Cisco CyberOps Associate CBROPS 200201 Chapter7:
Introduction to Security Operations Management.
Question 3:
Which NIST IR category stakeholder is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies?
A. CSIRT
B. PSIRT
C. public affairs
D. management
Correct Answer: D
Question 4:
Which attack represents the evasion technique of resource exhaustion?
A. SQL injection
B. man-in-the-middle
C. bluesnarfing
D. denial-of-service
Correct Answer: D
Reference: https://www.ciscopress.com/articles/article.asp?p=3100055andseqNum=3
Question 5:
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
A. fragmentation
B. pivoting
C. encryption
D. stenography
Correct Answer: C
Question 6:
What are the two differences between stateful and deep packet inspection? (Choose two )
A. Stateful inspection is capable of TCP state tracking, and deep packet filtering checks only TCP source and destination ports
B. Deep packet inspection is capable of malware blocking, and stateful inspection is not
C. Deep packet inspection operates on Layers 3 and 4. and stateful inspection operates on Layer 3 of the OSI model
D. Deep packet inspection is capable of TCP state monitoring only, and stateful inspection can inspect TCP and UDP.
E. Stateful inspection is capable of packet data inspections, and deep packet inspection is not
Correct Answer: AB
Question 7:
Which process is used when IPS events are removed to improve data integrity?
A. data availability
B. data normalization
C. data signature
D. data protection
Correct Answer: B
Question 8:
Refer to the exhibit.
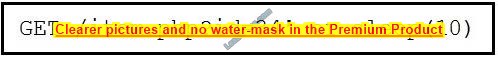
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
A. parameter manipulation
B. heap memory corruption
C. command injection
D. blind SQL injection
Correct Answer: D
Question 9:
Refer to the exhibit.

Which event is occurring?
A. A binary named “submit” is running on VM cuckoo1.
B. A binary is being submitted to run on VM cuckoo1
C. A binary on VM cuckoo1 is being submitted for evaluation
D. A URL is being evaluated to see if it has a malicious binary
Correct Answer: B
https://cuckoo.readthedocs.io/en/latest/usage/submit/
Question 10:
A user received an email attachment named “Hr405-report2609-empl094.exe” but did not run it. Which category of the cyber kill chain should be assigned to this type of event?
A. installation
B. reconnaissance
C. weaponization
D. delivery
Correct Answer: A
Question 11:
What causes events on a Windows system to show Event Code 4625 in the log messages?
A. The system detected an XSS attack
B. Someone is trying a brute force attack on the network
C. Another device is gaining root access to the system
D. A privileged user successfully logged into the system
Correct Answer: B
Question 12:
Which tool provides a full packet capture from network traffic?
A. Nagios
B. CAINE
C. Hydra
D. Wireshark
Correct Answer: D
Question 13:
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
A. Untampered images are used in the security investigation process
B. Tampered images are used in the security investigation process
C. The image has tampered if the stored hash and the computed hash match
D. Tampered images are used in the incident recovery process
E. The image is untampered if the stored hash and the computed hash match
Correct Answer: AE
Cert Guide by Omar Santos, Chapter 9 – Introduction to Digital Forensics. “When you collect evidence, you must protect its integrity. This involves making sure that nothing is added to the evidence and that nothing is deleted or destroyed (this is known as evidence preservation).”
Question 14:
An automotive company provides new types of engines and special brakes for rally sports cars. The company has a database of inventions and patents for their engines and technical information Customers can access the database through the company\’s website after they register and identify themselves. Which type of protected data is accessed by customers?
A. IP data
B. PII data
C. PSI data
D. PHI data
Correct Answer: B
Question 15:
The SOC team has confirmed a potential indicator of compromise on an endpoint. The team has narrowed the executable file\’s type to a new trojan family. According to the NIST Computer Security Incident Handling Guide, what is the next step in handling this event?
A. Isolate the infected endpoint from the network.
B. Perform forensics analysis on the infected endpoint.
C. Collect public information on the malware behavior.
D. Prioritize incident handling based on the impact.
Correct Answer: C
reference: https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-61r2.pdf
…
Lead4Pas provides 264 newly updated 200-201 exam questions and answers: https://www.leads4pass.com/200-201.html, practice the complete exam questions to help you easily pass the exam and get the Cisco Certified CyberOps Associate certification certificate.
Summarize:
CyberOps Associate certification is an independent core certification that can be obtained as long as candidates pass the Cisco 200-201 certification exam. Online practice tests can help you increase your knowledge and verify deficiencies.
Lead4Pass 200-201 dumps contain the latest updated 264 Cisco 200-201 exam questions and answers that are tailor-made for candidates to pass the most effectively.
Comments on 'The latest and valid Cisco 200-201 exam practice questions are shared online' (0)
Comments Feed
Comments are closed.