Latest 350-201 dumps & Free practice | 350-201 CBRCOR exam
Are you looking for the latest 350-201 dumps exam materials?
Lead4Pass shares the best exam materials for the 2023 350-201 certification exam, download the latest Lead4Pass 350-201 dumps: https://www.leads4pass.com/350-201.html, use PDF or
VCE practice tools help you practice the test and ensure you pass the exam with ease and success.
There are many learning methods, and the most efficient way is to practice. Participating in the 350-201 online practice test will help you understand your current learning situation and make the best judgment in the end, ensuring that you are 100% confident in preparing for the 350-201 certification exam.
350-201 Online Practice Test:
| Type | Number of exam questions | Exam name | Exam code | Verify answer |
| Free | 15 | Performing CyberOps Using Cisco Security Technologies (CBRCOR) | 350-201 | View |
Question 1:
What do 2xx HTTP response codes indicate for REST APIs?
A. additional action must be taken by the client to complete the request
B. the server takes responsibility for error status codes
C. communication of transfer protocol-level information
D. successful acceptance of the client\’s request
Question 2:
Refer to the exhibit. Which command was executed in PowerShell to generate this log?

A. Get-EventLog -LogName*
B. Get-EventLog -List
C. Get-WinEvent -ListLog* -ComputerName localhost
D. Get-WinEvent -ListLog*
Reference: https://lists.xymon.com/archive/2019-March/046125.html
Question 3:
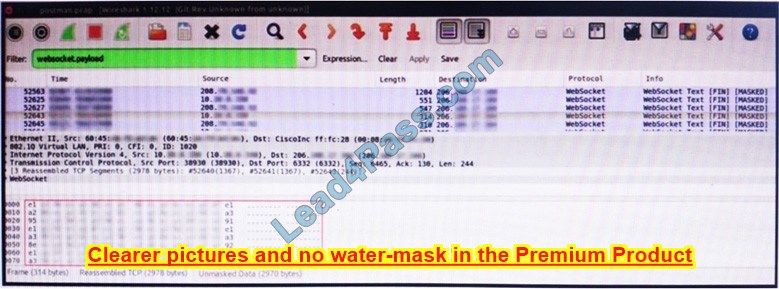
Refer to the exhibit. An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting suspicious network activity. The origin header for the direct IP connections in the packets was initiated by a google chrome extension on a WebSocket protocol. The engineer checked message payloads to determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?
A. The extension is not performing as intended because of restrictions since ports 80 and 443 should be accessible
B. The traffic is legitimate as the google chrome extension is reaching out to check for updates and fetches this information
C. There is a possible data leak because payloads should be encoded as UTF-8 text
D. There is malware that is communicating via encrypted channels to the command and control server
Question 4:
An engineer notices that every Sunday night, there is a two-hour period with a large load of network activity. Upon further investigation, the engineer finds that the activity is from locations around the globe outside the organization\’s service area. What are the next steps the engineer must take?
A. Assign the issue to the incident handling provider because no suspicious activity has been observed during business hours.
B. Review the SIEM and FirePower logs, block all traffic, and document the results of calling the call center.
C. Define the access points using StealthWatch or SIEM logs, understand services being offered during the hours in question, and cross-correlate other source events.
D. Treat it as a false positive, and accept the SIEM issue as valid to avoid alerts from triggering on weekends.
Question 5:
An employee who often travels abroad logs in from a first-seen country during non-working hours. The SIEM tool generates an alert that the user is forwarding an increased amount of emails to an external mail domain and then logs out. The investigation concludes that the external domain belongs to a competitor.
Which two behaviors triggered UEBA? (Choose two.)
A. domain belongs to a competitor
B. log in during non-working hours
C. email forwarding to an external domain
D. log in from a first-seen country
E. increased number of sent mails
Question 6:
Refer to the exhibit. Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE detects the threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a quarantine VLAN using Adaptive Network Control policy. Which method was used to signal ISE to quarantine the endpoints?
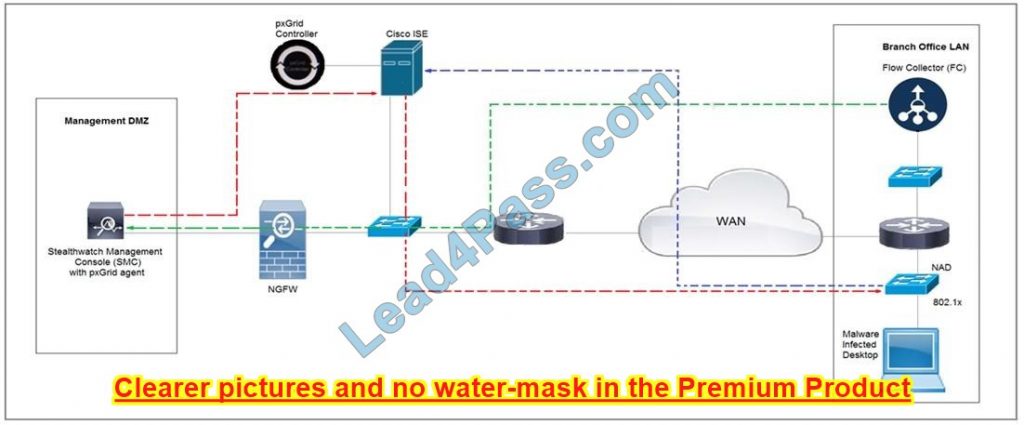
A. SNMP
B. Syslog
C. REST API
D. pxGrid
Question 7:
DRAG DROP
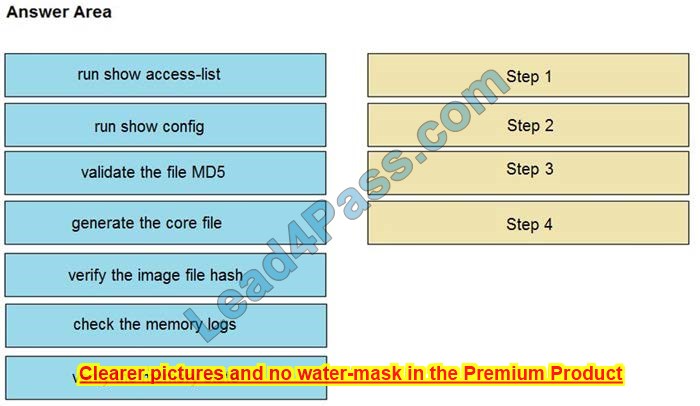
An organization lost connectivity to critical servers, and users cannot access business applications and internal websites. An engineer checks the network devices to investigate the outage and determines that all devices are functioning. Drag and drop the steps from the left into the sequence on the right to continue investigating this issue. Not all options are used.
Select and Place:
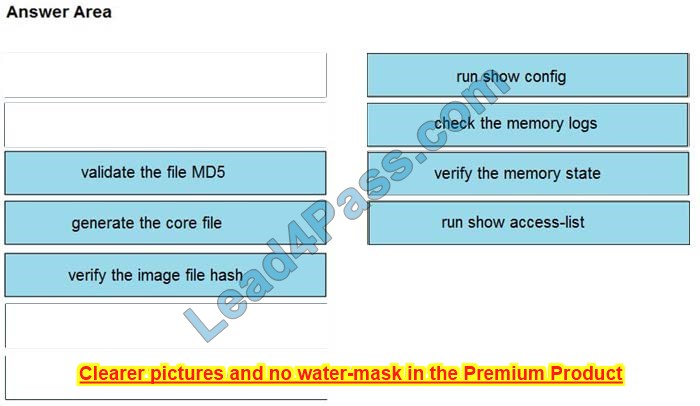
Correct Answer:
Question 8:
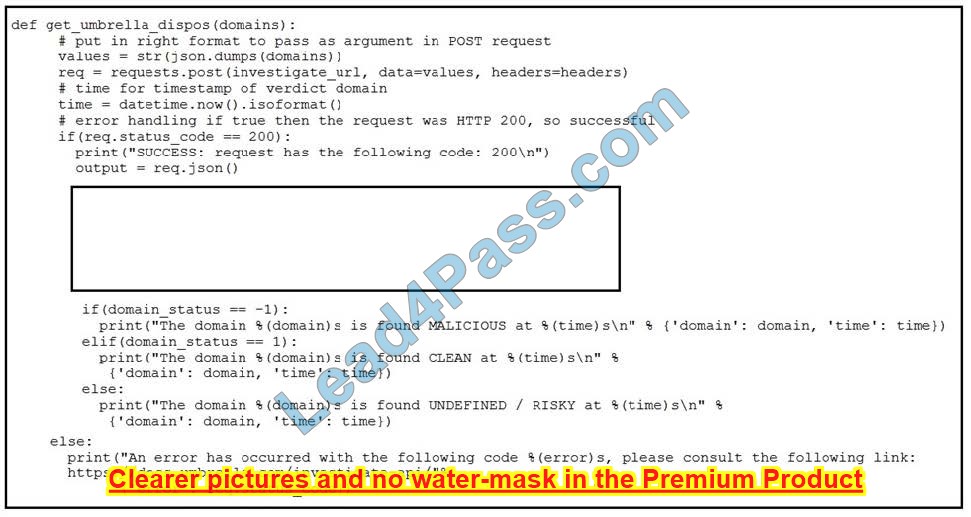
Refer to the exhibit. Which code snippet will parse the response to identify the status of the domain as malicious, clean or undefined?
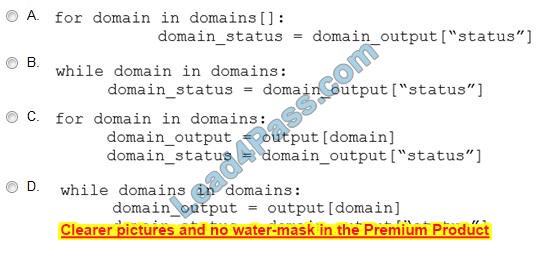
A. Option A
B. Option B
C. Option C
D. Option D
Question 9:
Refer to the exhibit. For IP 192.168.1.209, what are the risk level, activity, and next step?
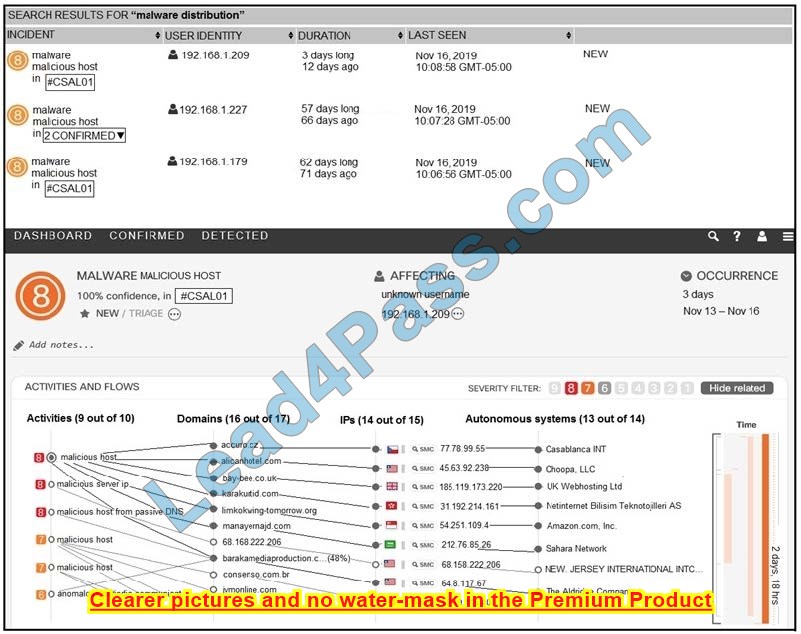
A. high risk level, anomalous periodic communication, quarantine with antivirus
B. critical risk level, malicious server IP, run in a sandboxed environment
C. critical risk level, data exfiltration, isolate the device
D. high-risk level, malicious host, investigate further
Question 10:
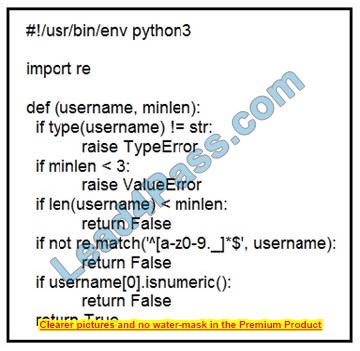
Refer to the exhibit. An organization is using an internal application for printing documents that requires a separate registration on the website. The application allows format-free user creation, and users must match these required conditions to comply with the company\’s user creation policy: minimum length: 3 usernames can only use letters, numbers, dots, and underscores usernames cannot begin with a number
The application administrator has to manually change and track these days to ensure compliance. An engineer is tasked to implement a script to automate the process according to the company user creation policy. The engineer implemented this piece of code within the application, but users are still able to create format-free usernames.
Which change is needed to apply the restrictions?
A. modify code to return error on restrictions def return false_user(username, minlen)
B. automate the restrictions def automate_user(username, minlen)
C. validate the restrictions, def validate_user(username, minlen)
D. modify code to force the restrictions, def force_user(username, minlen)
Question 11:
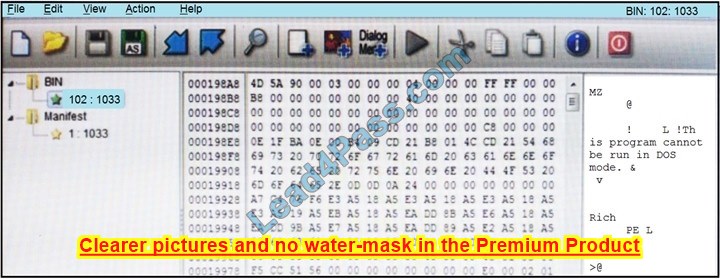
Refer to the exhibit. An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?
A. a DOS MZ executable format
B. an MS-DOS executable archive
C. an archived malware
D. a Windows executable file
Question 12:
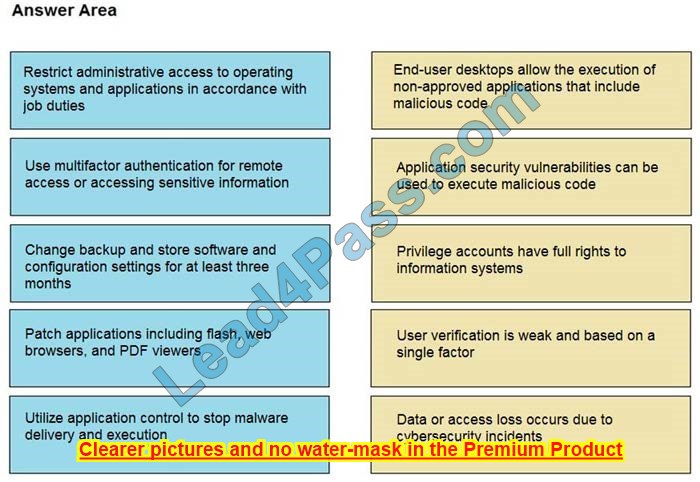
DRAG DROP
Drag and drop the mitigation steps from the left onto the vulnerabilities they mitigate on the right.
Select and Place:
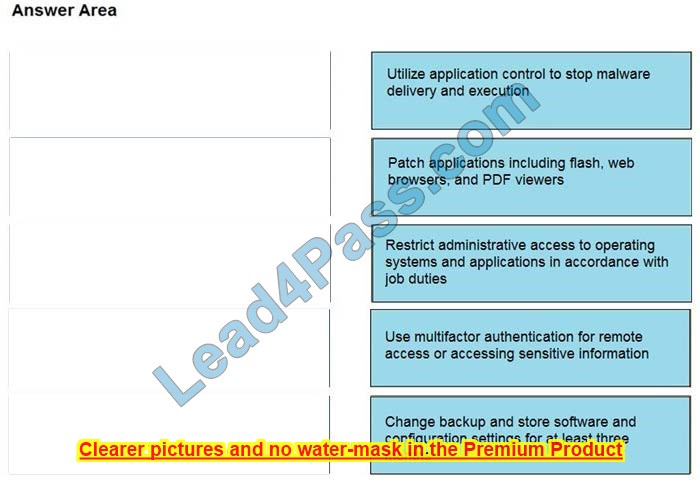
Correct Answer:
Question 13:
A threat actor attacked an organization\’s Active Directory server from a remote location, and in a thirty-minute timeframe, stole the password for the administrator account and attempted to access 3 company servers. The threat actor successfully accessed the first server that contained sales data, but no files were downloaded. A second server also accessed that contained marketing information and 11 files was downloaded. When the threat actor accessed the third server that contained corporate financial data, the session was disconnected, and the administrator\’s account was disabled.
Which activity triggered the behavior analytics tool?
A. accessing the Active Directory server
B. accessing the server with financial data
C. accessing multiple servers
D. downloading more than 10 files
Question 14:
Refer to the exhibit. Where is the MIME type that should be followed indicated?
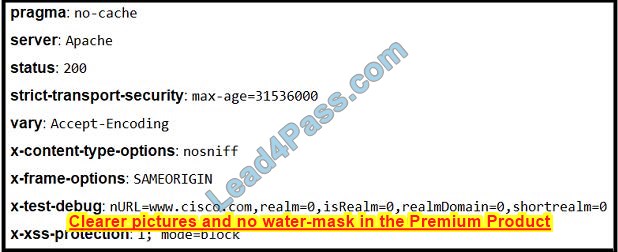
A. x-test-debug
B. strict-transport-security
C. x-xss-protection
D. x-content-type-options
Question 15:
DRAG DROP
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during the phases on the right.
Select and Place:
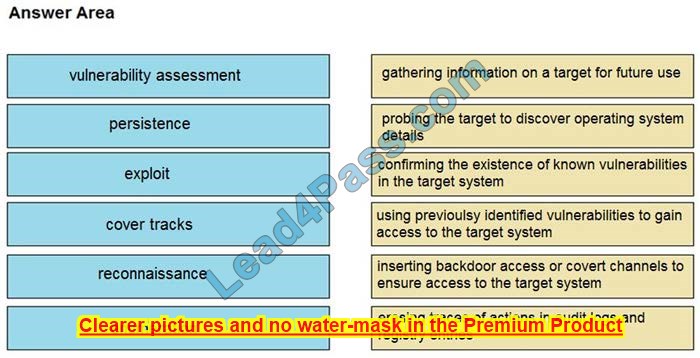
Correct Answer:
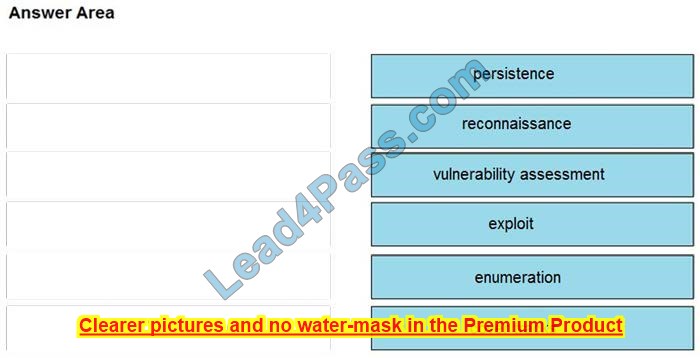
…
Verify answer:
| Number: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers: | D | A | C | A | AB | C | IMAGE | C | A | B | D | IMAGE | C | A | IMAGE |
Lead4Pass 350-201 dumps contain 139 latest exam questions and answers, download 350-201 dumps: https://www.leads4pass.com/350-201.html, practice the test carefully to make sure you pass the exam 100%.
Why use Lead4Pass 350-201 dumps?
If you are not confident to take the next exam, you can use 350-201 dumps to help you practice the test and help you pass the 350-201 CBRCOR exam. If you are fully prepared, you can also download 350-201 dumps for your to participate in A verification opportunity for the actual exam. The 350-201 dumps can be used as supplementary material as well as to verify your readiness for the actual exam.
Summarize:
This is a pleasure sharing, you can use the 350-201 online practice test to help you clarify your current learning situation, and download the real and effective Lead4Pass 350-201 DUMPS test materials to help you really solve the test questions.
Comments on 'Latest 350-201 dumps & Free practice | 350-201 CBRCOR exam' (0)
Comments Feed
Comments are closed.