[Update 2025] The latest and valid Cisco 200-201 exam practice questions are shared online

With the release of Cisco 200-201 CBROPS v1.2, new preparation materials must align with the latest changes, such as:
The addition of new concepts to the exam objectives, including:
- Cloud security deployments
- Threat modeling
- Attribute-based access control
- Temporal and environmental metrics
These additions aim to ensure candidates understand the latest security deployment terminology and concepts.
For this update, the Cisco 200-201 exam practice questions for 2025 have undergone significant changes, increasing from over 300 practice questions to 462 practice questions, fully covering the changes in v1.2.
Don’t worry! The main changes are in the name and certification path, with no substantial updates to the exam content. You can access the latest exam practice questions and answers at https://www.leads4pass.com/200-201.html.
200-201 CBROPS 2026 Changes
Starting from February 3, 2026, the original CBROPS exam will be renamed to “Understanding Cisco Cybersecurity Operations Fundamentals (CCNACBR).” At the same time, the related certification path will change from “Cybersecurity Associate” to “CCNA Cybersecurity” (also referred to as CCNACBR).
| Item | Current (CBROPS) | From 2026 (CCNACBR) |
|---|---|---|
| Exam Code / Name | 200-201 CBROPS | 200-201 CCNACBR |
| Certification Name | Cybersecurity Associate (formerly CyberOps Associate) | CCNA Cybersecurity (or CCNACBR) |
| Exam Content | No significant changes | Expected to remain the same (still covering security concepts, monitoring, host/network analysis, policies & procedures, etc.) |
| Transition | Current version still valid | Will automatically switch to the new version upon retirement, existing certifications remain valid |
If you are preparing for the exam today, you can still study using the “CBROPS” name, and upon passing, it will automatically be recognized as the new “CCNA Cybersecurity” (CCNACBR) certification.
If you plan to take the exam after February 2026, the related materials may have been updated to the new “CCNACBR” version, but the knowledge points remain the same.1.6s
The changes mentioned above won’t be implemented until 2026, so let’s study hard now!
Below are the latest study materials for 2025.
[2025] Cisco 200-201 Exam Practice Questions Online Share
| Number of exam questions | Related | Launch time |
| 15 (Free) | CyberOps Associate, CCNP | Sep 2025 |
New Question 1:
DRAG DROP
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
Select and Place:
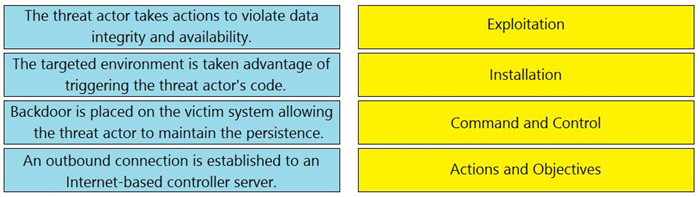
Correct Answer:
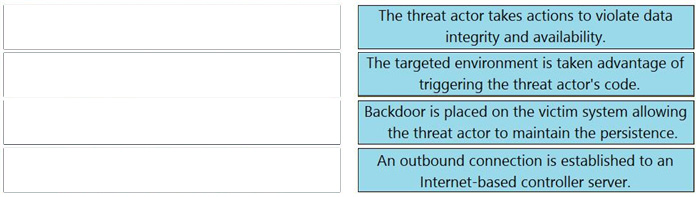
New Question 2:
Which event is user interaction?
A. gaining root access
B. executing remote code
C. reading and writing file permission
D. opening a malicious file
Correct Answer: D
New Question 3:
According to NIST, at which step of the incident response process should an organization apply lessons learned from practice?
A. preparation
B. detection and analysis
C. containment
D. post-incident activity
Correct Answer: D
New Question 4:
Which tool gives the ability to see session data in real time?
A. tcpdstat
B. trafdump
C. tcptrace
D. trafshow
Correct Answer: D
Explain:
“trafshow” is a tool that provides real-time information about network traffic sessions.
The tool captures and displays network packets and session data, allowing a network administrator to monitor network activity and troubleshoot problems.
“tcpdstat” and “tcptrace” are also network analysis tools, but they do not provide real-time monitoring. “trafdump” is not a valid tool name.
New Question 5:
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt.
Within 48 hours, multiple assets were breached, affecting the confidentiality of sensitive information.
What is the threat actor in this incident?
A. company assets that are threatened
B. customer assets that are threatened
C. perpetrators of the attack
D. victims of the attack
Correct Answer: B
New Question 6:
Which security monitoring data type is associated with application server logs?
A. transaction data
B. statistical data
C. session data
D. alert data
Correct Answer: A
New Question 7:
An engineer must investigate suspicious connections. Data has been gathered using a tcpdump command on a Linux device and saved as sandboxmalware2022-12-22.pcaps file.
The engineer is trying to open the tcpdump in the Wireshark tool. What is the expected result?
A. The file is opened.
B. The tool does not support Linux.
C. The file does not support the
Correct Answer: D
New Question 8:
What does the SOC metric MTTC provide in incident analysis?
A. average time it takes to recognize and stop the incident
B. average time it takes to fix the issues caused by the incident
C. average time it takes to detect that the incident has occurred
D. average time the attacker has access to the environment
Correct Answer: A
New Question 9:
Why is encryption challenging to security monitoring?
A. Encryption analysis is used by attackers to monitor VPN tunnels.
B. Encryption is used by threat actors as a method of evasion and obfuscation.
C. Encryption introduces additional processing requirements by the CPU.
D. Encryption introduces larger packet sizes to analyze and store.
Correct Answer: B
New Question 10:
Refer to the exhibit.
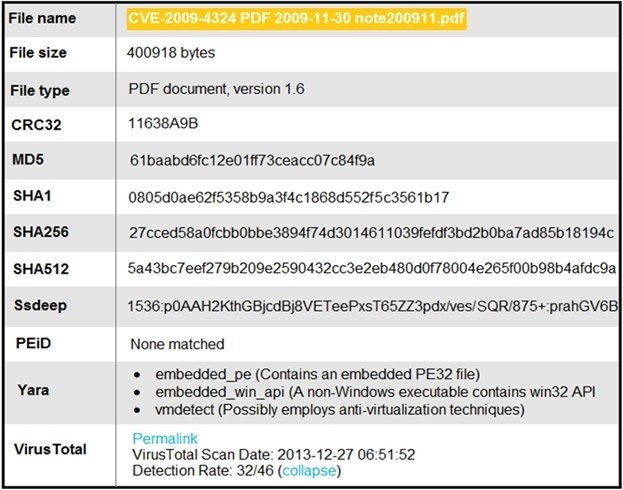
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
A. The file has an embedded executable and was matched by PEiD threat signatures for further analysis.
B. The file has an embedded non-Windows executable but no suspicious features are identified.
C. The file has an embedded Windows 32 executable and the Yara field lists suspicious features for further analysis.
D. The file was matched by PEiD threat signatures but no suspicious features are identified since the signature list is up to date.
Correct Answer: C
New Question 11:
What is the difference between deep packet inspection and stateful inspection?
A. Deep packet inspection gives insights up to Layer 7, and stateful inspection gives insights only up to Layer 4.
B. Deep packet inspection is more secure due to its complex signatures, and stateful inspection requires less human intervention.
C. Stateful inspection is more secure due to its complex signatures, and deep packet inspection requires less human intervention.
D. Stateful inspection verifies data at the transport layer and deep packet inspection verifies data at the application layer
Correct Answer: A
New Question 12:
What is a description of a man-in-the-middle network attack?
A. After attackers penetrate a network, they can use privilege escalation to expand their reach.
B. Attackers build botnets, large fleets of compromised devices, and use them to direct false traffic at networks or servers.
C. It involves attackers intercepting traffic, either between a network and external sites or within a network.
D. Attackers replicate malicious traffic as legitimate and bypass network protection solutions.
Correct Answer: C
New Question 13:
Which system monitors local system operation and local network access for violations of a security policy?
A. host-based intrusion detection
B. systems-based sandboxing
C. host-based firewall
D. antivirus
Correct Answer: A
Explain:
HIDS is capable of monitoring the internals of a computing system as well as the network packets on its network interfaces.
Host-based firewall is a piece of software running on a single Host that can restrict incoming and outgoing Network activity for that host only.
New Question 14:
According to CVSS, what is the attack vector?
A. set of steps taken by a threat actor before exploiting the vulnerability
B. process by which an attacker tries to exploit an existing vulnerability
C. context by which vulnerability exploitation is achievable
D. practical demonstration of an attack to understand the required tools and resources
Correct Answer: C
New Question 15:
An engineer is working on a ticket for an incident from the incident management team.
A week ago, an external web application was targeted by a DDoS attack. Server resources were exhausted and after two hours, it crashed.
An engineer was able to identify the attacker and technique used.
Three hours after the attack, the server was restored and the engineer recommended implementing mitigation by Blackhole filtering and transferred the incident ticket back to the IR team.
According to NIST.SP800-61, at which phase of the incident response did the engineer finish work?
A. post-incident activity
B. preparation
C. detection and analysis
D. containment, eradication, and recovery
Correct Answer: D
…
The above Cisco 200-201 exam practice questions are designed to help you warm up and familiarize yourself with the latest question types and formats.
You are welcome to download the latest exam practice questions and answers for 200-201 CBROPS v1.2 at: https://www.leads4pass.com/200-201.html (Total Questions: 462 Q&A) to help you successfully pass the exam and obtain the new “CCNA Cybersecurity” (CCNACBR) certification by preparing under the “CBROPS” name.
Summarize:
CyberOps Associate certification is an independent core certification that can be obtained as long as candidates pass the Cisco 200-201 certification exam. Online practice tests can help you increase your knowledge and verify deficiencies.
Leads4pass 200-201 dumps contain the latest updated 462 Cisco 200-201 exam questions and answers that are tailor-made for candidates to pass the most effectively.
Comments on '[Update 2025] The latest and valid Cisco 200-201 exam practice questions are shared online' (0)
Comments Feed
Comments are closed.